[5] Brama dla obiektów Ceph
18 lipca 2020Włączymy teraz Ceph Object Gateway (RADOSGW) aby uzyskać dostęp do zasobów klastra Ceph za pomocą Amazon S3 lub OpenStack Swift za pomocą kompatybilnego API.
Schemat sieci przedstawia się następująco.
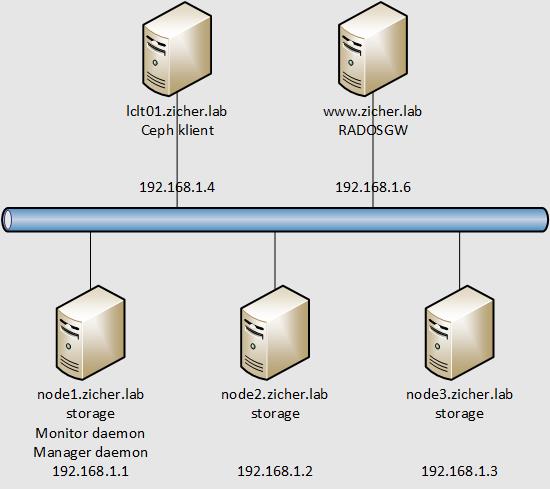
[1] przetransferuj potrzebne pliki na węzeł RADOSGW i skonfiguruj go z Admin Node.
# przetransferuj klucz publiczny [root@node1 ~]# ssh-copy-id www /usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/root/.ssh/id_rsa.pub" The authenticity of host 'www (192.168.1.6)' can't be established. ECDSA key fingerprint is SHA256:xCSfk21sQFwJhliPbBPX2XKMsivyZLuNzGRs03N3HoU. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes /usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed /usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys root@www's password: # wpisz hasło root'a@www Number of key(s) added: 1 Now try logging into the machine, with: "ssh 'www'" and check to make sure that only the key(s) you wanted were added. # zainstaluj wymagane pakiety [root@node1 ~]# ssh www "dnf -y install centos-release-ceph-octopus epel-release" [root@node1 ~]# ssh www "dnf -y install ceph-radosgw" [root@node1 ~]# mcedit /etc/ceph/ceph.conf # dodaj na końcu # client.rgw.(NazwaWęzła) [client.rgw.www] # adres IP węzła host = 192.168.1.6 # port nasłuchiwania rgw frontends = "civetweb port=8080" # nazwa DNS węzła rgw dns name = www.zicher.lab # transfer plików [root@node1 ~]# scp /etc/ceph/ceph.conf www:/etc/ceph/ ceph.conf 100% 385 18.3KB/s 00:00 [root@node1 ~]# scp /etc/ceph/ceph.client.admin.keyring www:/etc/ceph/ ceph.client.admin.keyring 100% 151 3.7KB/s 00:00 # konfiguracja RADOSGW [root@node1 ~]# ssh www "mkdir -p /var/lib/ceph/radosgw/ceph-rgw.www; ceph auth get-or-create client.rgw.www osd 'allow rwx' mon 'allow rw' -o /var/lib/ceph/radosgw/ceph-rgw.www/keyring; chown ceph. /etc/ceph/ceph.*; chown -R ceph. /var/lib/ceph/radosgw; systemctl enable --now ceph-radosgw@rgw.www; firewall-cmd --add-port=8080/tcp --permanent; firewall-cmd --reload" # potwierdź status # jest OK, jeśli widzisz podobną odpowiedź [root@node1 ~]# curl www.zicher.lab:8080 <?xml version="1.0" encoding="UTF-8"?><ListAllMyBucketsResult xmlns="http://s3.amazonaws.com/doc/2006-03-01/"><Owner><ID>anonymous</ID><DisplayName></DisplayName></Owner><Buckets></Buckets></ListAllMyBucketsResult>
[2] Na węźle Geteway stwórz kompatybilnego użytkownika, który będzie się mógł się uwierzytelnić na Getaway’u.
# stworzymy użytkownika [zicherlab] [root@www ~]# radosgw-admin user create --uid=zicherlab --display-name="Laboratorium Zicherki" --email=admin@zicher.lab { "user_id": "zicherlab", "display_name": "Laboratorium Zicherki", "email": "admin@zicher.lab", "suspended": 0, "max_buckets": 1000, "subusers": [], "keys": [ { "user": "zicherlab", "access_key": "R2LGVF08R99WXGQS41VR", "secret_key": "txhtmLnLIbpy8SNb5g7MASszRLSvl75tow2soAmn" } ], "swift_keys": [], "caps": [], "op_mask": "read, write, delete", "default_placement": "", "default_storage_class": "", "placement_tags": [], "bucket_quota": { "enabled": false, "check_on_raw": false, "max_size": -1, "max_size_kb": 0, "max_objects": -1 }, "user_quota": { "enabled": false, "check_on_raw": false, "max_size": -1, "max_size_kb": 0, "max_objects": -1 }, "temp_url_keys": [], "type": "rgw", "mfa_ids": [] } # zobaczmy liczbę użytkowników [root@www ~]# radosgw-admin user list [ "zicherlab" ] [root@www ~]# radosgw-admin user info --uid=zicherlab { "user_id": "zicherlab", "display_name": "Laboratorium Zicherki", "email": "admin@zicher.lab", "suspended": 0, "max_buckets": 1000, "subusers": [], "keys": [ { "user": "zicherlab", "access_key": "R2LGVF08R99WXGQS41VR", "secret_key": "txhtmLnLIbpy8SNb5g7MASszRLSvl75tow2soAmn" } ], "swift_keys": [], "caps": [], "op_mask": "read, write, delete", "default_placement": "", "default_storage_class": "", "placement_tags": [], "bucket_quota": { "enabled": false, "check_on_raw": false, "max_size": -1, "max_size_kb": 0, "max_objects": -1 }, "user_quota": { "enabled": false, "check_on_raw": false, "max_size": -1, "max_size_kb": 0, "max_objects": -1 }, "temp_url_keys": [], "type": "rgw", "mfa_ids": [] }
[3] Zweryfikujmy dostęp za pomocą interfejsu S3 i stworzymy testowy skrypt na komputerze.
# instalujemy z EPEL [root@lclt01 ~]# dnf --enablerepo=epel -y install python3-boto3 [root@lclt01 ~]# mcedit s3_test.py import sys import boto3 from botocore.config import Config # klucze użytkownika, które stworzyłeś/dodałeś w [2] session = boto3.session.Session( aws_access_key_id = 'R2LGVF08R99WXGQS41VR', aws_secret_access_key = 'txhtmLnLlbpy8SNb5g7MASszRLSvl75tow2soAmn' ) # URL Geteway'a s3client = session.client( 's3', endpoint_url = 'http://192.168.1.6:8080', config = Config() ) # tworzymy nowy BUCKET [moje-wiadro] bucket = s3client.create_bucket(Bucket = 'moje-wiadro') # lista BUCKET'ów print(s3client.list_buckets()) # kasujemy [moje-wiadro] s3client.delete_bucket(Bucket = 'moje-wiadro') [root@lclt01 ~]# python3 s3_test.py {'ResponseMetadata': {'RequestId': 'tx000000000000000000005-005f13297e-5e4f-default', 'HostId': '', 'HTTPStatusCode': 200, 'HTTPHeaders': {'transfer-encoding': 'chunked', 'x-amz-request-id': 'tx000000000000000000005-005f13297e-5e4f-default', 'content-type': 'application/xml', 'date': 'Sat, 18 Jul 2020 16:55:26 GMT'}, 'RetryAttempts': 0}, 'Buckets': [{'Name': 'moje-wiadro', 'CreationDate': datetime.datetime(2020, 7, 18, 16, 55, 21, 396000, tzinfo=tzutc())}], 'Owner': {'DisplayName': 'Laboratorium Zicherki', 'ID': 'zicherlab'}}