[7] FreeIPA – Replikacja
7 lutego 2021Skonfigurujemy teraz opcje replikacji serwera FreeIPA. W tym przykładzie sieć będzie wyglądała następująco:
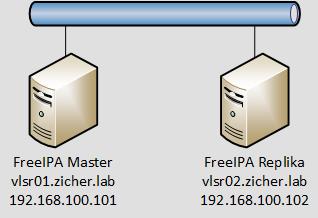
1. Skonfiguruj klienta FreeIPA, który ma pełnić funkcję repliki: [3] FreeIPA – konfiguracja klienta
2. Na serwerze (głównym) FreeIPA dodaj host, który będzie repliką tego serwera – czyli dodaj go do grupy [ipaservers]. Ponadto musi mieć on możliwość rozwiązywania adresów na hoście głównym i hoście repliki. Jeśli używasz zintegrowanego DNS FreeIPA, ale nie ustawiłeś strefy odwrotnej, skonfiguruj ją
[root@vlsr01 ~]# ipa hostgroup-add-member ipaservers –hosts vlsr02.zicher.lab
Grupa komputerów: ipaservers
Opis: IPA server hosts
Element komputerów: vlsr01.zicher.lab, vlsr02.zicher.lab
—————————
Liczba dodanych elementów 1
—————————
# jeżeli serwer nie posiada odwrotnej strefy w DNS skonfiguruj jak poniżej
# poniższy przykład jest dla sieci [192.168.100.0/24]
[root@vlsr01 ~]# ipa dnszone-add 100.168.192.in-addr.arpa
Nazwa strefy: 100.168.192.in-addr.arpa.
Aktywna strefa: TRUE
Authoritative nameserver: vlsr01.zicher.lab.
Adres e-mail administratora: hostmaster
Numer seryjny SOA: 1612637102
Odświeżenie SOA: 3600
Ponowienie SOA: 900
Wygaszenie SOA: 1209600
Minimalne SOA: 3600
Polityka aktualizacji BIND: grant ZICHER.LAB krb5-subdomain 100.168.192.in-addr.arpa. PTR;
Dynamic update: FALSE
Allow query: any;
Allow transfer: none;
# dodaj rekordy PTR w strefie odwrotnej
[root@vlsr01 ~]# ipa dnsrecord-add 100.168.192.in-addr.arpa 101 –ptr-rec vlsr01.zicher.lab.
Record name: 101
PTR record: vlsr01.zicher.lab.
[root@vlsr01 ~]# ipa dnsrecord-add 100.168.192.in-addr.arpa 102 –ptr-rec vlsr02.zicher.lab.
Record name: 102
PTR record: vlsr02.zicher.lab.
# jeżeli Firewalld jest uruchomiony to zezwól na ruch następującym usługom
[root@vlsr01 ~]# firewall-cmd –add-service=freeipa-replication –permanent
[root@vlsr01 ~]# firewall-cmd –reload
3. Skonfiguruj teraz host, który będzie repliką
# jeżeli firewalld jest uruchomiony zezwól na następujące usługi [root@vlsr02 ~]# firewall-cmd --add-service={freeipa-ldap,freeipa-ldaps,dns,ntp,freeipa-replication} --permanent [root@vlsr02 ~]# firewall-cmd –reload [root@vlsr02 ~]# dnf module -y install idm:DL1/dns # skonfiguruj replikację # jeśli masz ustawiony forward dla DNS, wpisz [--forwarder=XXX.XXX.XXX.XXX] [root@vlsr02 ~]# ipa-replica-install --setup-ca --setup-dns --no-forwarders Lookup failed: Preferred host vlsr02.zicher.lab does not provide DNS. Run connection check to master Connection check OK Disabled p11-kit-proxy Configuring directory server (dirsrv). Estimated time: 30 seconds [1/38]: creating directory server instance [2/38]: tune ldbm plugin [3/38]: adding default schema [4/38]: enabling memberof plugin [5/38]: enabling winsync plugin [6/38]: configure password logging [7/38]: configuring replication version plugin [8/38]: enabling IPA enrollment plugin [9/38]: configuring uniqueness plugin [10/38]: configuring uuid plugin [11/38]: configuring modrdn plugin [12/38]: configuring DNS plugin [13/38]: enabling entryUSN plugin [14/38]: configuring lockout plugin [15/38]: configuring topology plugin [16/38]: creating indices [17/38]: enabling referential integrity plugin [18/38]: configuring certmap.conf [19/38]: configure new location for managed entries [20/38]: configure dirsrv ccache and keytab [21/38]: enabling SASL mapping fallback [22/38]: restarting directory server [23/38]: creating DS keytab [24/38]: ignore time skew for initial replication [25/38]: setting up initial replication Starting replication, please wait until this has completed. Update in progress, 3 seconds elapsed Update succeeded [26/38]: prevent time skew after initial replication [27/38]: adding sasl mappings to the directory [28/38]: updating schema [29/38]: setting Auto Member configuration [30/38]: enabling S4U2Proxy delegation [31/38]: initializing group membership [32/38]: adding master entry [33/38]: initializing domain level [34/38]: configuring Posix uid/gid generation [35/38]: adding replication acis [36/38]: activating sidgen plugin [37/38]: activating extdom plugin [38/38]: configuring directory to start on boot Done configuring directory server (dirsrv). Replica DNS records could not be added on master: Insufficient access: Insufficient 'add' privilege to add the entry 'idnsname=vlsr02,idnsname=zicher.lab.,cn=dns,dc=zicher,dc=lab'. Configuring Kerberos KDC (krb5kdc) [1/5]: configuring KDC [2/5]: adding the password extension to the directory [3/5]: creating anonymous principal [4/5]: starting the KDC [5/5]: configuring KDC to start on boot Done configuring Kerberos KDC (krb5kdc). Configuring kadmin [1/2]: starting kadmin [2/2]: configuring kadmin to start on boot Done configuring kadmin. Configuring directory server (dirsrv) [1/3]: configuring TLS for DS instance [2/3]: importing CA certificates from LDAP [3/3]: restarting directory server Done configuring directory server (dirsrv). Configuring the web interface (httpd) [1/21]: stopping httpd [2/21]: backing up ssl.conf [3/21]: disabling nss.conf [4/21]: configuring mod_ssl certificate paths [5/21]: setting mod_ssl protocol list [6/21]: configuring mod_ssl log directory [7/21]: disabling mod_ssl OCSP [8/21]: adding URL rewriting rules [9/21]: configuring httpd Nothing to do for configure_httpd_wsgi_conf [10/21]: setting up httpd keytab [11/21]: configuring Gssproxy [12/21]: setting up ssl [13/21]: configure certmonger for renewals [14/21]: publish CA cert [15/21]: clean up any existing httpd ccaches [16/21]: configuring SELinux for httpd [17/21]: create KDC proxy config [18/21]: enable KDC proxy [19/21]: starting httpd [20/21]: configuring httpd to start on boot [21/21]: enabling oddjobd Done configuring the web interface (httpd). Configuring ipa-otpd [1/2]: starting ipa-otpd [2/2]: configuring ipa-otpd to start on boot Done configuring ipa-otpd. Custodia uses 'vlsr01.zicher.lab' as master peer. Configuring ipa-custodia [1/4]: Generating ipa-custodia config file [2/4]: Generating ipa-custodia keys [3/4]: starting ipa-custodia [4/4]: configuring ipa-custodia to start on boot Done configuring ipa-custodia. Configuring certificate server (pki-tomcatd). Estimated time: 3 minutes [1/28]: creating certificate server db [2/28]: setting up initial replication Starting replication, please wait until this has completed. Update in progress, 5 seconds elapsed Update succeeded [3/28]: creating ACIs for admin [4/28]: creating installation admin user [5/28]: configuring certificate server instance [6/28]: stopping certificate server instance to update CS.cfg [7/28]: backing up CS.cfg [8/28]: Add ipa-pki-wait-running [9/28]: secure AJP connector [10/28]: reindex attributes [11/28]: exporting Dogtag certificate store pin [12/28]: disabling nonces [13/28]: set up CRL publishing [14/28]: enable PKIX certificate path discovery and validation [15/28]: authorizing RA to modify profiles [16/28]: authorizing RA to manage lightweight CAs [17/28]: Ensure lightweight CAs container exists [18/28]: destroying installation admin user [19/28]: starting certificate server instance [20/28]: Finalize replication settings [21/28]: configure certmonger for renewals [22/28]: Importing RA key [23/28]: configure certificate renewals [24/28]: Configure HTTP to proxy connections [25/28]: updating IPA configuration [26/28]: enabling CA instance [27/28]: configuring certmonger renewal for lightweight CAs [28/28]: deploying ACME service Done configuring certificate server (pki-tomcatd). Configuring Kerberos KDC (krb5kdc) [1/1]: installing X509 Certificate for PKINIT Done configuring Kerberos KDC (krb5kdc). Applying LDAP updates Upgrading IPA:. Estimated time: 1 minute 30 seconds [1/10]: stopping directory server [2/10]: saving configuration [3/10]: disabling listeners [4/10]: enabling DS global lock [5/10]: disabling Schema Compat [6/10]: starting directory server [7/10]: upgrading server [8/10]: stopping directory server [9/10]: restoring configuration [10/10]: starting directory server Done. Finalize replication settings Restarting the KDC dnssec-validation yes Configuring DNS (named) [1/8]: generating rndc key file [2/8]: setting up our own record [3/8]: adding NS record to the zones [4/8]: setting up kerberos principal [5/8]: setting up named.conf created new /etc/named.conf created named user config '/etc/named/ipa-ext.conf' created named user config '/etc/named/ipa-options-ext.conf' [6/8]: setting up server configuration [7/8]: configuring named to start on boot [8/8]: changing resolv.conf to point to ourselves Done configuring DNS (named). Restarting the web server to pick up resolv.conf changes Configuring DNS key synchronization service (ipa-dnskeysyncd) [1/7]: checking status [2/7]: setting up bind-dyndb-ldap working directory [3/7]: setting up kerberos principal [4/7]: setting up SoftHSM [5/7]: adding DNSSEC containers DNSSEC container exists (step skipped) [6/7]: creating replica keys [7/7]: configuring ipa-dnskeysyncd to start on boot Done configuring DNS key synchronization service (ipa-dnskeysyncd). Restarting ipa-dnskeysyncd Restarting named Updating DNS system records Global DNS configuration in LDAP server is empty You can use 'dnsconfig-mod' command to set global DNS options that would override settings in local named.conf files The ipa-replica-install command was successful
4. Po zakończeniu normalnej konfiguracji replikacji można znaleźć istniejące konta użytkowników lub dodać nowe konta na hoście replikacji.
[root@vlsr02 ~]# kinit admin
Password for admin@ZICHER.LAB: # wpisz hasło
[root@vlsr02 ~]# ipa user-find
---------------------
Pasuje 4 użytkowników
---------------------
Login użytkownika: admin
Nazwisko: Administrator
Katalog domowy: /home/admin
Powłoka logowania: /bin/bash
Principal alias: admin@ZICHER.LAB, root@ZICHER.LAB
UID: 766200000
GID: 766200000
Account disabled: False
Login użytkownika: pierwszy
Imię: Pierwszy
Nazwisko: Pierwszy
Katalog domowy: /home/pierwszy
Powłoka logowania: /bin/sh
Nazwa naczelnika: pierwszy@ZICHER.LAB
Principal alias: pierwszy@ZICHER.LAB
Adres e-mail: pierwszy@zicher.lab
UID: 766200004
GID: 766200004
Account disabled: False
Login użytkownika: user01
Imię: Uzytkownik
Nazwisko: user01
Katalog domowy: /home/user01
Powłoka logowania: /bin/sh
Nazwa naczelnika: user01@ZICHER.LAB
Principal alias: user01@ZICHER.LAB
Adres e-mail: user01@zicher.lab
UID: 766200003
GID: 766200003
Account disabled: False
Login użytkownika: useripa
Imię: Uzytkownik
Nazwisko: FreeIPA
Katalog domowy: /home/useripa
Powłoka logowania: /bin/sh
Nazwa naczelnika: useripa@ZICHER.LAB
Principal alias: useripa@ZICHER.LAB
Adres e-mail: useripa@zicher.lab
UID: 766200001
GID: 766200001
Account disabled: False
----------------------------
Number of entries returned 4
----------------------------