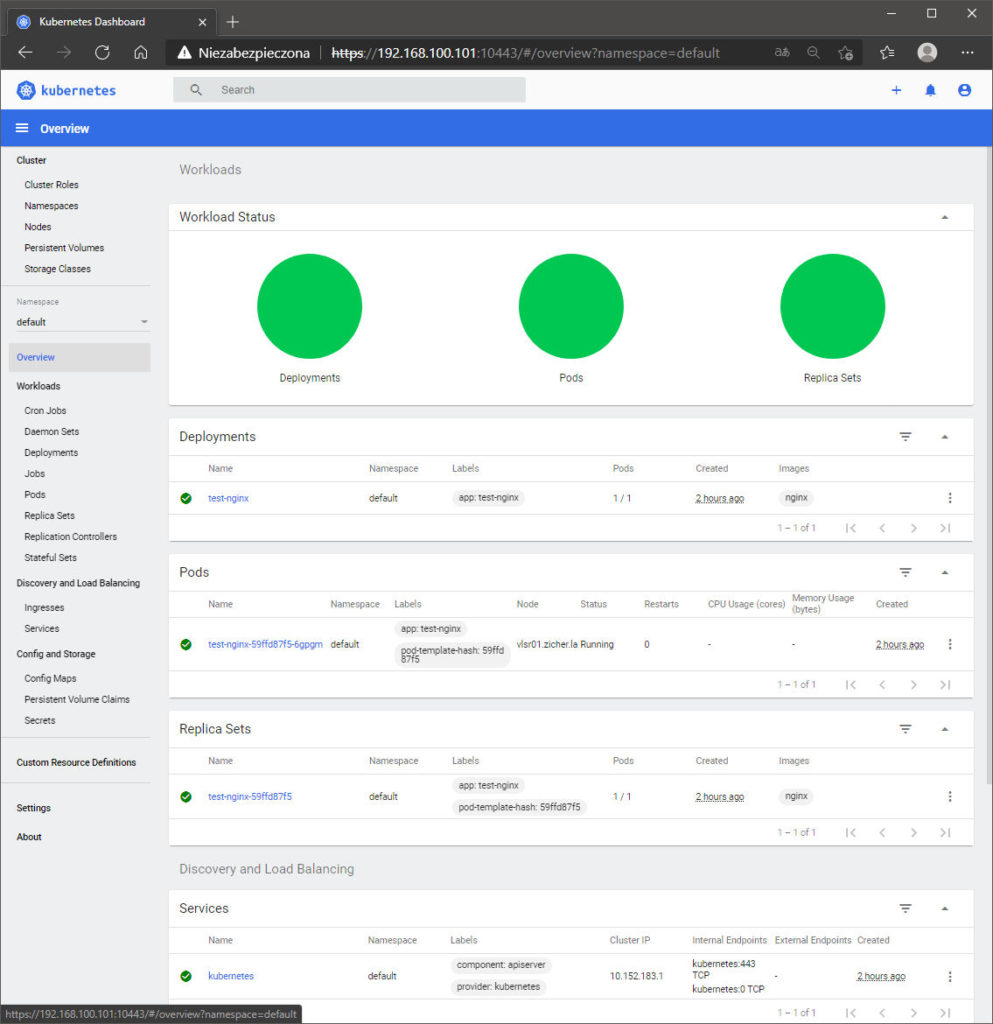
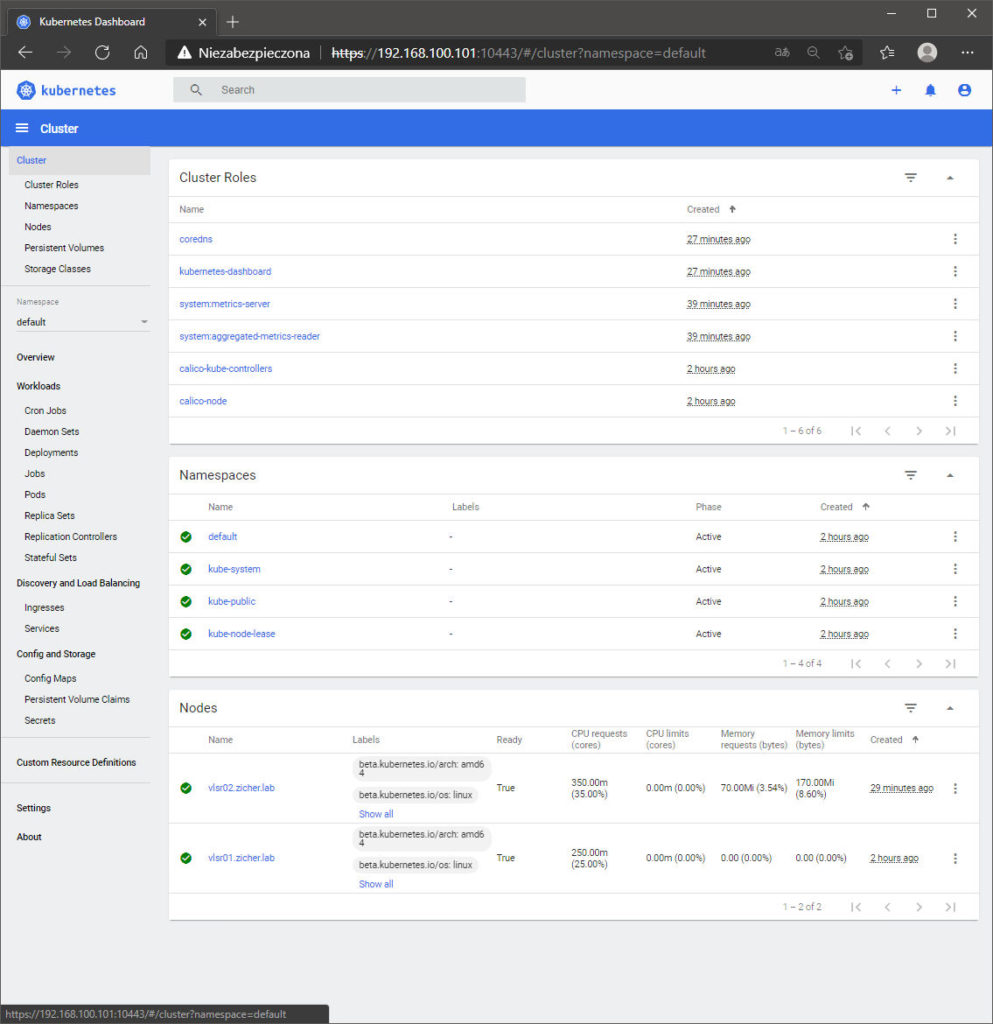
[4] MicroK8s – WebPanel
11 lutego 2021Aby włączyć zarządzanie za pomocą strony WWW, postępuj jak poniżej.
[1] Włącz przystawkę [dashboard] na głównym węźle.
[root@vlsr01 ~]# microk8s enable dashboard dns Enabling Kubernetes Dashboard Addon metrics-server is already enabled. Applying manifest serviceaccount/kubernetes-dashboard created service/kubernetes-dashboard created secret/kubernetes-dashboard-certs created secret/kubernetes-dashboard-csrf created secret/kubernetes-dashboard-key-holder created configmap/kubernetes-dashboard-settings created role.rbac.authorization.k8s.io/kubernetes-dashboard created clusterrole.rbac.authorization.k8s.io/kubernetes-dashboard created rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created clusterrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created deployment.apps/kubernetes-dashboard created service/dashboard-metrics-scraper created deployment.apps/dashboard-metrics-scraper created If RBAC is not enabled access the dashboard using the default token retrieved with: token=$(microk8s kubectl -n kube-system get secret | grep default-token | cut -d " " -f1) microk8s kubectl -n kube-system describe secret $token In an RBAC enabled setup (microk8s enable RBAC) you need to create a user with restricted permissions as shown in: https://github.com/kubernetes/dashboard/blob/master/docs/user/access-control/creating-sample-user.md Enabling DNS Applying manifest serviceaccount/coredns created configmap/coredns created deployment.apps/coredns created service/kube-dns created clusterrole.rbac.authorization.k8s.io/coredns created clusterrolebinding.rbac.authorization.k8s.io/coredns created Restarting kubelet Adding argument --cluster-domain to nodes. Configuring node 192.168.100.102 Configuring node 192.168.100.101 Adding argument --cluster-dns to nodes. Configuring node 192.168.100.102 Configuring node 192.168.100.101 Restarting nodes. Configuring node 192.168.100.102 Configuring node 192.168.100.101 DNS is enabled [root@vlsr01 ~]# microk8s kubectl get services -n kube-system NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE metrics-server ClusterIP 10.152.183.254 <none> 443/TCP 14m kubernetes-dashboard ClusterIP 10.152.183.77 <none> 443/TCP 73s dashboard-metrics-scraper ClusterIP 10.152.183.28 <none> 8000/TCP 73s kube-dns ClusterIP 10.152.183.10 <none> 53/UDP,53/TCP,9153/TCP 72s [root@vlsr01 ~]# microk8s kubectl -n kube-system get pods -o wide NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES metrics-server-8bbfb4bdb-x2rrq 1/1 Running 0 14m 10.1.86.196 vlsr01.zicher.lab <none> <none> dashboard-metrics-scraper-6c4568dc68-xg6fx 1/1 Running 0 83s 10.1.206.2 vlsr02.zicher.lab <none> <none> calico-node-vq9h7 1/1 Running 0 4m10s 192.168.100.102 vlsr02.zicher.lab <none> <none> calico-kube-controllers-847c8c99d-mv2g6 1/1 Running 0 111m 10.1.86.194 vlsr01.zicher.lab <none> <none> calico-node-574jj 1/1 Running 0 105m 192.168.100.101 vlsr01.zicher.lab <none> <none> kubernetes-dashboard-7ffd448895-zwj5x 1/1 Running 0 83s 10.1.206.3 vlsr02.zicher.lab <none> <none> coredns-86f78bb79c-g5xtc 1/1 Running 0 82s 10.1.206.1 vlsr02.zicher.lab <none> <none> # potwierdź token # Token znajduje się w drugiej kolumnie w linii: [token: ] [root@vlsr01 ~]# microk8s kubectl -n kube-system describe secret $(microk8s kubectl -n kube-system get secret | grep default-token | awk '{print $1}') Name: default-token-kgc98 Namespace: kube-system Labels: <none> Annotations: kubernetes.io/service-account.name: default kubernetes.io/service-account.uid: 80e3568b-1d70-4b51-abdb-637a43ce925c Type: kubernetes.io/service-account-token Data ==== ca.crt: 1103 bytes namespace: 11 bytes token: eyJhbGciOiJSUzI1NiIsImtpZCI6IkpxS2dEWHhQS0g3c1N4TUFfSmNvSHFJYXYyVi1YQ0VjQ2FZb1ZzMGYwVmsifQ.eyJpcte-Hhrvn4l-9dwnV5jFD9nLRUC_HpIieiRVcHW9zqp1W1SZCdz6nrZ30Whaadd3uYOBKdfBmXTz5_5XBaPCi-cAkpeErKA # ustaw przekierowanie portów, aby móc uzyskać dostęp z zewnątrz [root@vlsr01 ~]# microk8s kubectl port-forward -n kube-system service/kubernetes-dashboard --address 0.0.0.0 10443:443 & Forwarding from 0.0.0.0:10443 -> 8443 # jeżeli Firewalld jest uruchomiony należy zezwolić na ruch na następującym porcie [root@vlsr01 ~]# firewall-cmd --add-port=10443/tcp --permanent [root@vlsr01 ~]# firewall-cmd –reload
[2] Przejdź na adres [https://MicroK8s_pierwszy_węzeł (nazwa hosta lub adres IP):10443/] w przeglądarce z jakiegokolwiek hosta w tej samej sieci. Skopiuj token, który potwierdziłeś w [1] w wierszu [potwierdź token].
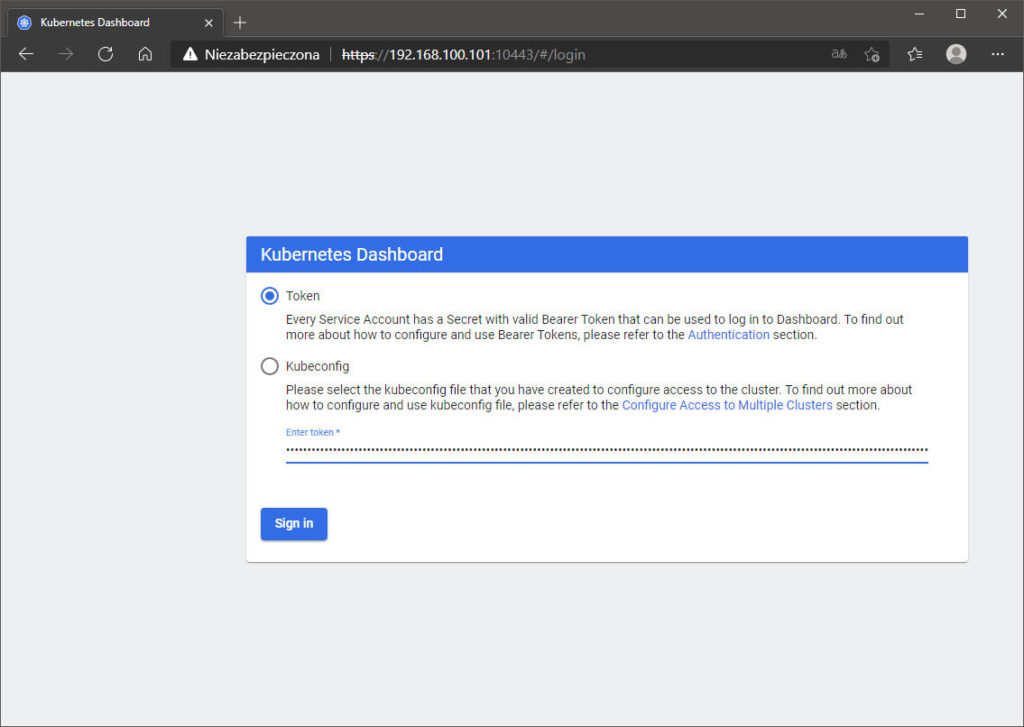
Wklej go do pola [Enter token] i naciśnij [Sign in].
[3] Zostaniesz zalogowany do panelu zarządzania.