[14] httpd – mod_security
23 stycznia 2022Włączymy moduł [mod_security]aby skonfigurować Web Application Firewall (WAF).
[1] Zainstaluj [mod_security].
[root@vlsr01 ~]# dnf install mod_security
[2] Po zainstalowaniu pliki konfiguracyjne są umieszczane w katalogu, jak poniżej, a ustawienie jest włączone. Niektóre ustawienia są już włączone, możesz również dodać własne reguły.
[root@vlsr01 ~]# cat /etc/httpd/conf.d/mod_security.conf <IfModule mod_security2.c> # Default recommended configuration SecRuleEngine On SecRequestBodyAccess On SecRule REQUEST_HEADERS:Content-Type "text/xml" \ "id:'200000',phase:1,t:none,t:lowercase,pass,nolog,ctl:requestBodyProce ssor=XML" SecRequestBodyLimit 13107200 SecRequestBodyNoFilesLimit 131072 SecRequestBodyInMemoryLimit 131072 SecRequestBodyLimitAction Reject SecRule REQBODY_ERROR "!@eq 0" \ . . . . .
[3] Jeśli chcesz, możesz pisać własne reguły – jak poniżej.
SecRule VARIABILES OPERATOR [ACTIONS]
Parametry mają wiele wartości, zalecam zapoznanie się z nimi na oficjalnej stronie: https://github.com/SpiderLabs/ModSecurity/wiki
[4] Dla przykładu skonfigurujemy kilka reguł i sprawdzimy poprawność ich działania.
[root@vlsr01 ~]# mcedit /etc/httpd/modsecurity.d/local_rules/modsecurity_localrules.conf SecDefaultAction "phase:2,deny,log,status:406" SecRule REQUEST_URI "etc/passwd" "id:'500001'" SecRule REQUEST_URI "\.\./" "id:'500002'" SecRule ARGS "<[Ss][Cc][Rr][Ii][Pp][Tt]" "id:'500003'" SecRule ARGS "[Ss][Ee][Ll][Ee][Cc][Tt][[:space:]]+[Ff][Rr][Oo][Mm]" "id:'500004'"
[5] Uzyskaj dostęp do URI, który posiada ustawione wcześniej słowa i sprawdź czy działa normalnie.
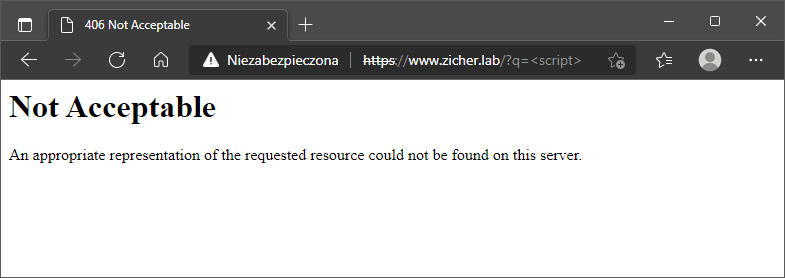
[6] Dzienniki dla [mod_security] są umieszczane w katalogu w następujący sposób.
[root@vlsr01 ~]# cat /var/log/httpd/modsec_audit.log --ef04744f-A-- [23/Jan/2022:21:01:30 +0100] Ye20Ghj3gQSEhSU0uacTHgAAAAE 192.168.100.171 63480 192.168.100.101 443 --ef04744f-B-- GET /?q=%3Cscript%3E HTTP/1.1 Host: www.zicher.lab Connection: keep-alive sec-ch-ua: " Not;A Brand";v="99", "Microsoft Edge";v="97", "Chromium";v="97" sec-ch-ua-mobile: ?0 sec-ch-ua-platform: "Windows" Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.99 Safari/537.36 Edg/97.0.1072.69 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Sec-Fetch-Site: none Sec-Fetch-Mode: navigate Sec-Fetch-User: ?1 Sec-Fetch-Dest: document Accept-Encoding: gzip, deflate, br Accept-Language: pl,en;q=0.9,en-GB;q=0.8,en-US;q=0.7,zh-TW;q=0.6,zh;q=0.5,id;q=0.4 Cookie: csrftoken=DcwH0KW0veWgRqKpbBRFN4u4WtWCk80GC6yEVkZMPeYcXsAnty0FB1mNBFqhF2gl; sessionid=tr18k5y7ltg4v0ez64q4uwrxg0fsezsa --ef04744f-F-- HTTP/1.1 406 Not Acceptable Content-Length: 249 Keep-Alive: timeout=5, max=100 Connection: Keep-Alive Content-Type: text/html; charset=iso-8859-1 --ef04744f-E-- --ef04744f-H-- Message: Access denied with code 406 (phase 2). Pattern match "<[Ss][Cc][Rr][Ii][Pp][Tt]" at ARGS:q. [file "/etc/httpd/modsecurity.d/local_rules/modsecurity_localrules.conf"] [line "4"] [id "500003"] Apache-Error: [file "apache2_util.c"] [line 273] [level 3] [client 192.168.100.171] ModSecurity: Access denied with code 406 (phase 2). Pattern match "<[Ss][Cc][Rr][Ii][Pp][Tt]" at ARGS:q. [file "/etc/httpd/modsecurity.d/local_rules/modsecurity_localrules.conf"] [line "4"] [id "500003"] [hostname "www.zicher.lab"] [uri "/"] [unique_id "Ye20Ghj3gQSEhSU0uacTHgAAAAE"] Action: Intercepted (phase 2) Stopwatch: 1642968090051699 459 (- - -) Stopwatch2: 1642968090051699 459; combined=22, p1=6, p2=15, p3=0, p4=0, p5=1, sr=0, sw=0, l=0, gc=0 Response-Body-Transformed: Dechunked Producer: ModSecurity for Apache/2.9.2 (http://www.modsecurity.org/). Server: Apache Engine-Mode: "ENABLED" --ef04744f-Z--
[7] Ogólne zasady pochodzą z oficjalnego repozytorium i można je łatwo zastosować w poniższy sposób. Musisz jednak dostosować je do swoich własnych witryn internetowych, aby nie blokować niezbędnych żądań.
[root@vlsr01 ~]# dnf install mod_security_crs # zasady są umieszczone w następujący sposób # są połączone z katalogiem [/etc/httpd/modsecurity.d/activated_rules] [root@vlsr01 ~]# ll /usr/share/mod_modsecurity_crs/rules/ razem 668 -rw-r--r--. 1 root root 786 2021-06-24 crawlers-user-agents.data -rw-r--r--. 1 root root 551 2021-06-24 iis-errors.data -rw-r--r--. 1 root root 933 2021-06-24 java-classes.data -rw-r--r--. 1 root root 264 2021-06-24 java-code-leakages.data -rw-r--r--. 1 root root 240 2021-06-24 java-errors.data -rw-r--r--. 1 root root 31209 2021-06-24 lfi-os-files.data -rw-r--r--. 1 root root 5409 2021-06-24 php-config-directives.data -rw-r--r--. 1 root root 9201 2021-06-24 php-errors.data -rw-r--r--. 1 root root 683 2021-06-24 php-function-names-933150.data -rw-r--r--. 1 root root 21282 2021-06-24 php-function-names-933151.data -rw-r--r--. 1 root root 224 2021-06-24 php-variables.data -rw-r--r--. 1 root root 13513 2021-06-24 REQUEST-901-INITIALIZATION.conf -rw-r--r--. 1 root root 13069 2021-06-24 REQUEST-903.9001-DRUPAL-EXCLUSION-RULES.conf -rw-r--r--. 1 root root 25812 2021-06-24 REQUEST-903.9002-WORDPRESS-EXCLUSION-RULES.conf -rw-r--r--. 1 root root 10642 2021-06-24 REQUEST-903.9003-NEXTCLOUD-EXCLUSION-RULES.conf -rw-r--r--. 1 root root 7822 2021-06-24 REQUEST-903.9004-DOKUWIKI-EXCLUSION-RULES.conf -rw-r--r--. 1 root root 1876 2021-06-24 REQUEST-903.9005-CPANEL-EXCLUSION-RULES.conf -rw-r--r--. 1 root root 18336 2021-06-24 REQUEST-903.9006-XENFORO-EXCLUSION-RULES.conf -rw-r--r--. 1 root root 1555 2021-06-24 REQUEST-905-COMMON-EXCEPTIONS.conf -rw-r--r--. 1 root root 10448 2021-06-24 REQUEST-910-IP-REPUTATION.conf -rw-r--r--. 1 root root 2614 2021-06-24 REQUEST-911-METHOD-ENFORCEMENT.conf -rw-r--r--. 1 root root 10743 2021-06-24 REQUEST-912-DOS-PROTECTION.conf -rw-r--r--. 1 root root 7069 2021-06-24 REQUEST-913-SCANNER-DETECTION.conf -rw-r--r--. 1 root root 50184 2021-06-24 REQUEST-920-PROTOCOL-ENFORCEMENT.conf -rw-r--r--. 1 root root 13208 2021-06-24 REQUEST-921-PROTOCOL-ATTACK.conf -rw-r--r--. 1 root root 5958 2021-06-24 REQUEST-930-APPLICATION-ATTACK-LFI.conf -rw-r--r--. 1 root root 5678 2021-06-24 REQUEST-931-APPLICATION-ATTACK-RFI.conf -rw-r--r--. 1 root root 54798 2021-06-24 REQUEST-932-APPLICATION-ATTACK-RCE.conf -rw-r--r--. 1 root root 32617 2021-06-24 REQUEST-933-APPLICATION-ATTACK-PHP.conf -rw-r--r--. 1 root root 3927 2021-06-24 REQUEST-934-APPLICATION-ATTACK-NODEJS.conf -rw-r--r--. 1 root root 40398 2021-06-24 REQUEST-941-APPLICATION-ATTACK-XSS.conf -rw-r--r--. 1 root root 70457 2021-06-24 REQUEST-942-APPLICATION-ATTACK-SQLI.conf -rw-r--r--. 1 root root 5204 2021-06-24 REQUEST-943-APPLICATION-ATTACK-SESSION-FIXATION.conf -rw-r--r--. 1 root root 15288 2021-06-24 REQUEST-944-APPLICATION-ATTACK-JAVA.conf -rw-r--r--. 1 root root 4094 2021-06-24 REQUEST-949-BLOCKING-EVALUATION.conf -rw-r--r--. 1 root root 4714 2021-06-24 RESPONSE-950-DATA-LEAKAGES.conf -rw-r--r--. 1 root root 17863 2021-06-24 RESPONSE-951-DATA-LEAKAGES-SQL.conf -rw-r--r--. 1 root root 3515 2021-06-24 RESPONSE-952-DATA-LEAKAGES-JAVA.conf -rw-r--r--. 1 root root 4951 2021-06-24 RESPONSE-953-DATA-LEAKAGES-PHP.conf -rw-r--r--. 1 root root 5764 2021-06-24 RESPONSE-954-DATA-LEAKAGES-IIS.conf -rw-r--r--. 1 root root 4207 2021-06-24 RESPONSE-959-BLOCKING-EVALUATION.conf -rw-r--r--. 1 root root 6801 2021-06-24 RESPONSE-980-CORRELATION.conf -rw-r--r--. 1 root root 2043 2021-06-24 restricted-files.data -rw-r--r--. 1 root root 390 2021-06-24 restricted-upload.data -rw-r--r--. 1 root root 216 2021-06-24 scanners-headers.data -rw-r--r--. 1 root root 418 2021-06-24 scanners-urls.data -rw-r--r--. 1 root root 4869 2021-06-24 scanners-user-agents.data -rw-r--r--. 1 root root 717 2021-06-24 scripting-user-agents.data -rw-r--r--. 1 root root 1894 2021-06-24 sql-errors.data -rw-r--r--. 1 root root 1380 2021-06-24 unix-shell.data -rw-r--r--. 1 root root 3920 2021-06-24 windows-powershell-commands.data